
Epicor DMT: Data Management Tool Tips & Tricks

The Magic of Epicor DMT Licensing
A common user challenge over the years with Epicor’s Data Management Tool (DMT) relates to the licensing of the actual module. Epicor DMT came from a very different evolutionary thread than the main application, and when trying to bind these threads, things often become tangled.
Licensing can be especially twisted, and more than a few us have felt the frustration of figuring out just who to send the license request to. Then remembering that we needed to cull the list of Company IDs from the database to be licensed. Then anxiously waiting for the returned file to arrive, hoping that we weren’t going to receive, by accident, a license file configured for a manufacturer of manure spreaders, headquartered in Glasgow.
But fear not, dear users. Epicor provides us a DMT remedy. For versions less than 10.02.5xx, you will still need to send Epicor a list of your Company IDs so that they can generate the appropriate license file for your use. But for versions 10.02.5xx and above, the DMT license is now included as part of your E10 license and is no longer reliant on your Company IDs.
As you can see below, DMT can now be licensed through Epicor’s standard license, which removes the need to drop individual DMT license files in user client folders. This greatly simplifies the deployment of the Epicor DMT application.
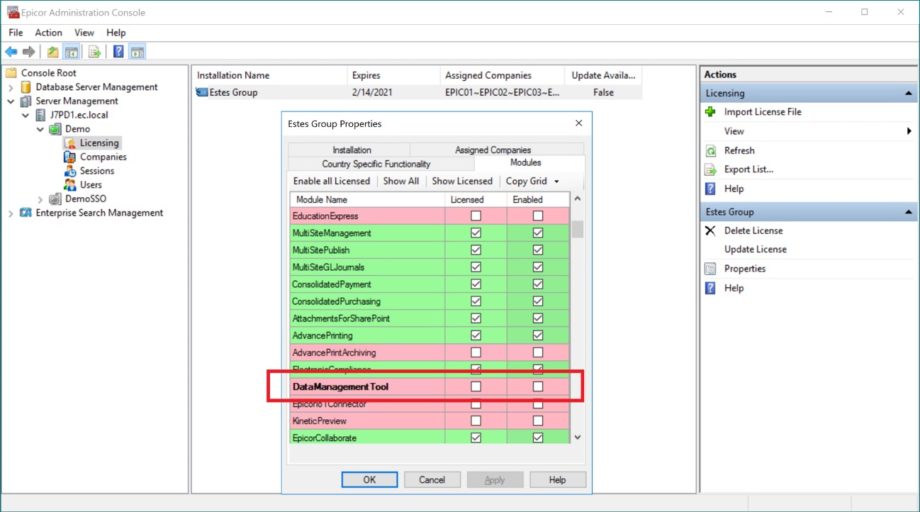
That said, there are a couple of related tricks that can help you separate the forks from the sporks in your Epicor kitchen. One way to identify your DMT licensing from the DMT application itself is to utilize the settings icon at the bottom of the application and open the “DMT License Info”:
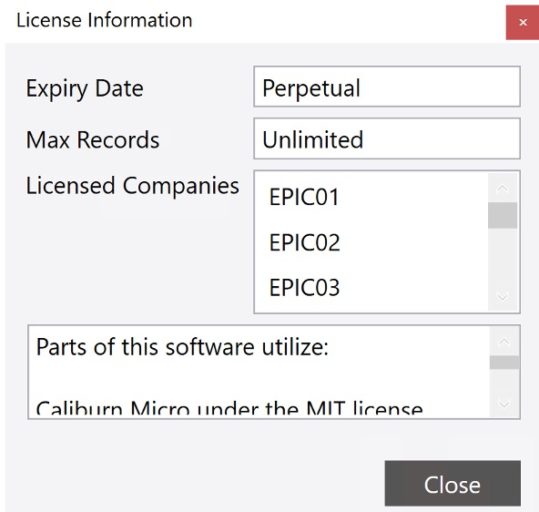
This will raise a properties window, providing details about the DMT license:
DMT is a client-based application. Therefore, much of the magic behind the DMT module is to be found in the application’s client folder. This includes licensing. Going back to our talk about license, it’s important to understand that for a DMT client to function correctly, one of the following must be the case:
• DMT must be licensed in Epicor’s Standard License file, which is installed on the application server.
• A traditional DMT .lic file must be deployed in the user’s client folder, where the DMT application normally resides.
Let us, as an example, assume we’re in a situation in which DMT is not licensed through the Admin Console license file. In lieu of the main license, a DMT-specific .lic file will need to reside in the client folder:
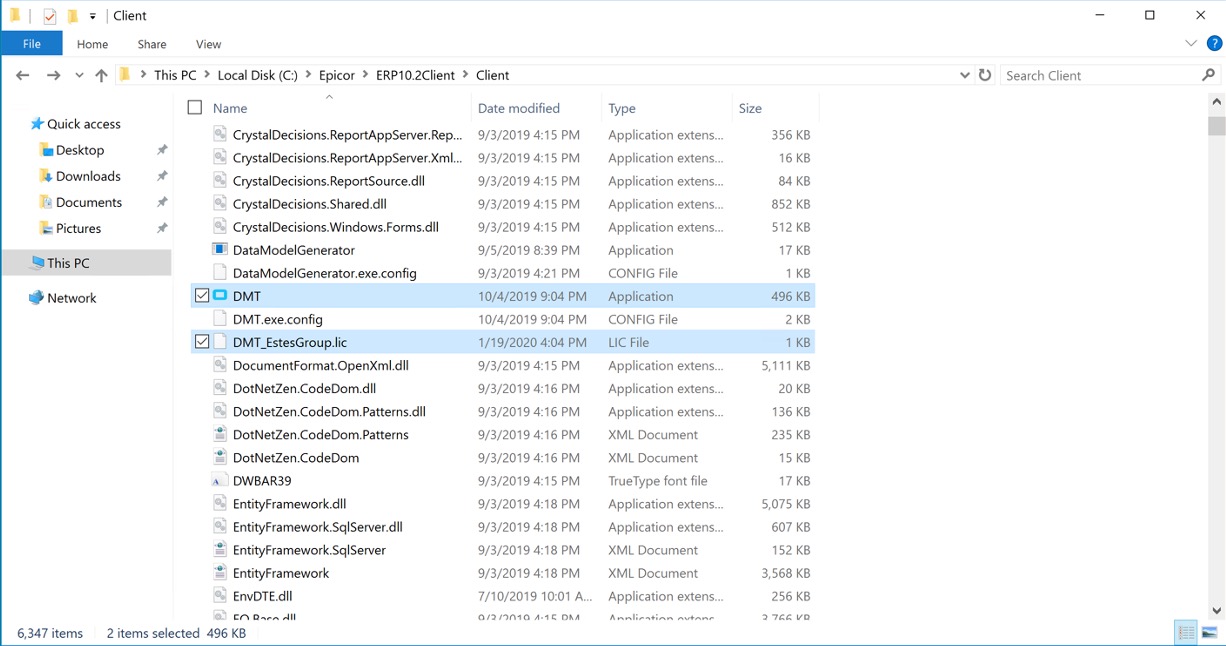
Were I to remove the .lic file from the client folder…
…upon my attempt to log into DMT, I will receive a licensing error:
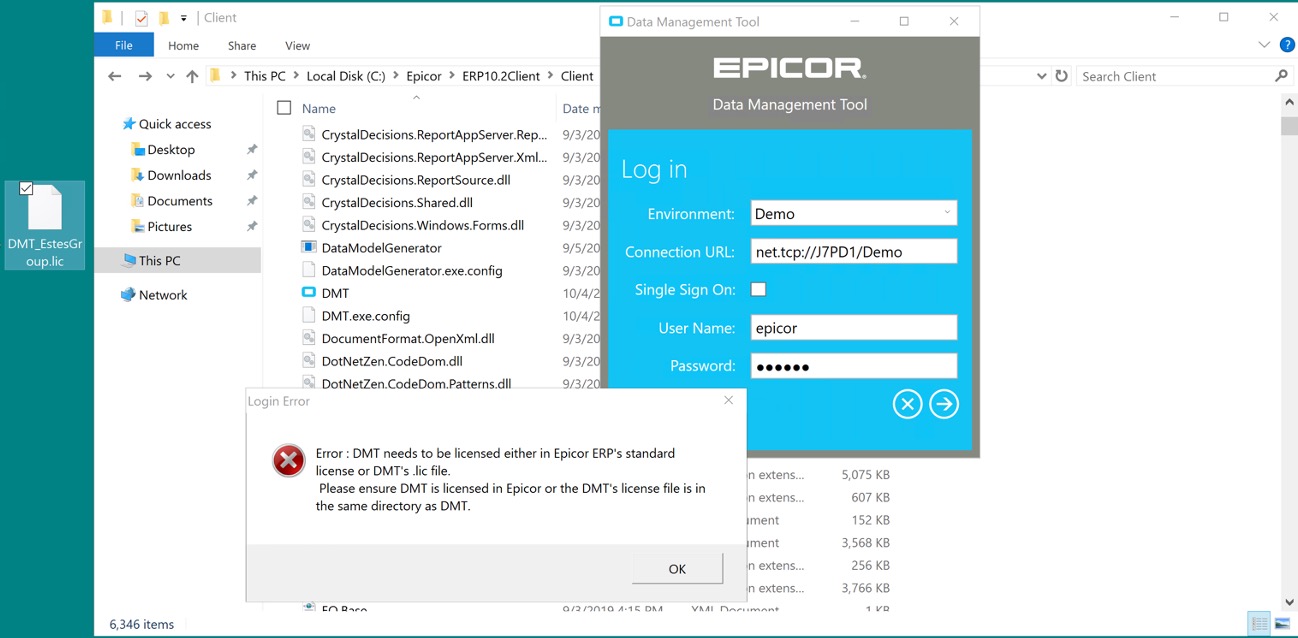
As such, if you don’t have the DMT module licensed through the Admin Console, you’ll need to make sure you’re still planting the company-specific license file in the appropriate client folders. If you think about it in the sense of a cooking motif, you can think of it as a situation in which the pantry is emptier than Mother Hubbard’s cupboard, the grocery store delivery is still a day out, and your mask is at the bottom of the laundry basket. Sometimes you need to cook with only what’s already in your house. Just like your dinner occasionally falls together as a tasty combination of tomato soup and wanton noodles, you’ll sometimes need to get a company-configured license file and stick it in your client folder. With these steps, you can get the Epicor DMT program to run.






