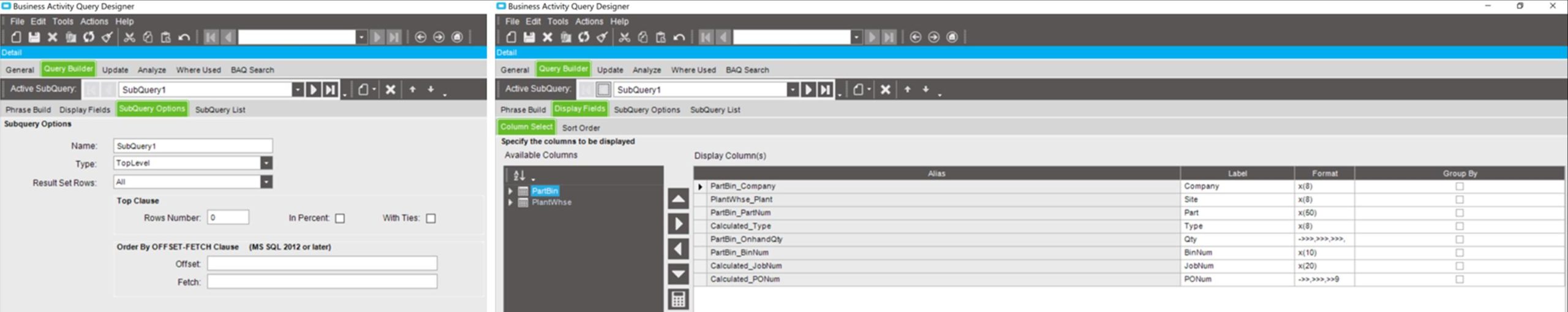
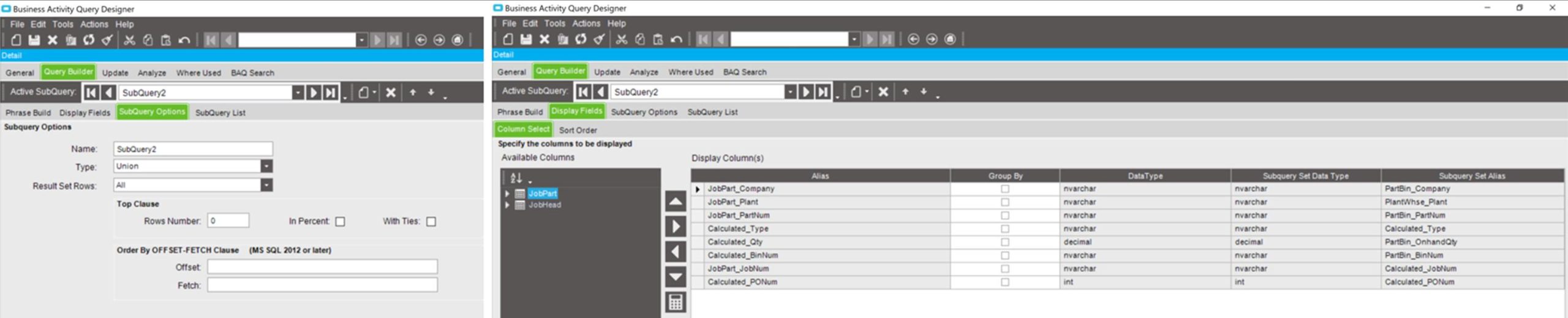
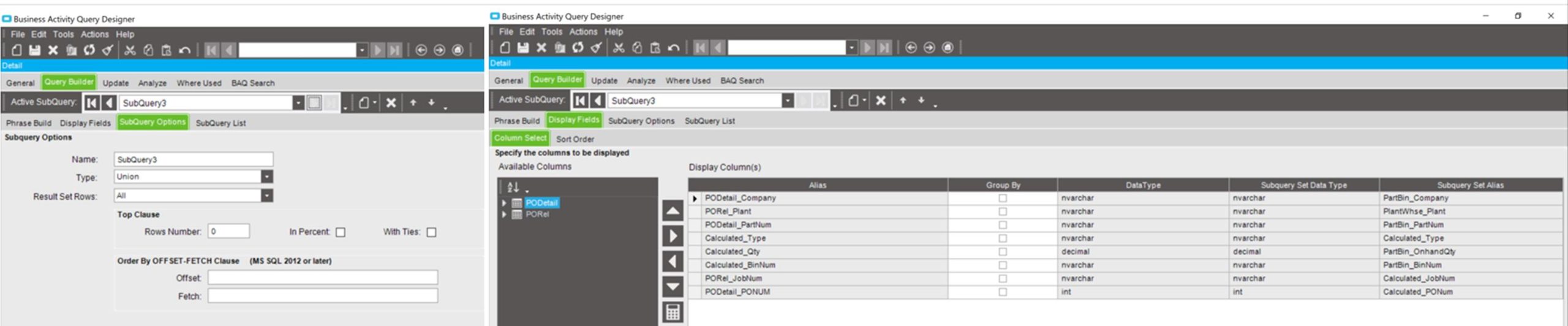
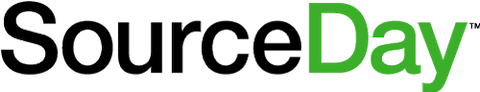What Cloud is Your Cloud Provider On?
ERP Hosting is Better Than a Trip to the Ice Cream Parlor
The age of “mass customization” pervades many areas of our business and personal lives. The general populace has grown accustomed to being able to “dial in” solutions as needed, especially when it comes to products and services. Tailored solutions have become a competitive advantage, if not a necessity, these days, and every cloud provider claims variety and customizability, even in the ever-so rigid atmosphere of SaaS (Software as a Service). If you’re looking for a cloud provider for your ERP (enterprise resource planning) application, do you ask where your new infrastructure team will actually cloud your data?
Ice cream parlors have been playing the variety card for decades. I have always been a fan of a good sundae—a little of this, a sprinkle of that, one flavor, two… the combinations are endless, as are the effects on my palate. But no two ice cream parlors are created equal. Similarly, no two cloud providers are created equal. Sometimes it feels like there are no standards that govern what it exactly means to be “flexible” in the cloud or to have “scalability” in the cloud. Like with ice cream parlors, sometimes vanilla is nothing more than artificial vanilla flavoring. This means that as a cloud solutions buyer, you need to understand the unique build of your server infrastructure before you sign the cloud services agreement.

In the cloud computing world, an ice cream sundae model for ERP application deployment is a natural progression of the mass customization movement. After all, flexibility and scalability are defining features of cloud computing.
Nevertheless, the big players in cloud solutions continue to pull us back into a world of vanilla (or vanilla flavoring). Tiered pricing models, service bundles, rigid step-progressions, and consumption models that do not adjust for seasonality leave many cloud customers feeling like they are trapped in an artificial vanilla apocalypse. Cloud computing is defined by its flexibility, but you wouldn’t know this when reading the fine print of your IT service contract.
That is to say, application deployment is not a one-size-fits-all proposition, even if your cloud provider is positioning it in that manner.
Some customers, with small footprints and standard business requirements, fit nicely within a software as a service (SaaS) framework when it comes to deploying ERP systems. However, many customers of greater size and complexity struggle with the limitations of SaaS. They want levels of access and control that are not normally afforded by SaaS deployment models. But exactly what a customer wants and needs differs from customer to customer. For suppliers offering very rigid solution sets, this can be a problem.
Some customers want a level of access and control that SaaS can’t support. They still want their cloud server stack micro-managed, but they don’t have the internal resources to perform the management. These customers lean toward managed ERP hosting, which falls more closely under a platform as a service (PaaS) model, where the solution provider manages the infrastructure and application platform layers, and the customer consumes the final output.
Other customers have the in-house staff and expertise to manage their own architecture. They want the solution provider to set up an ecosystem, but intend to take ownership and management of that ecosystem thereafter. These folks don’t need managed hosting, as they can perform any micro-management themselves. The solutions to satisfy these customers fall more under an infrastructure as a service (IaaS) model, where the solution provider provides the infrastructure, and the management of the application layer is the client’s responsibility.
But such simple distinctions between PaaS and IaaS seem too rigid for many customers. Many customers want something in between. They desire a combination of service, access, control, and responsibility. A sprinkle of this, a dash of that, a little smooth, a little crunchy.
As a customer, you need to make sure your cloud solution provider can lay out the various features and options that comprise their solution and help you work though a combination that fits your business. This might involve user provisioning, backup and disaster recovery, performance monitoring and tuning, or general application administration. Whatever the case, make sure your cloud solution provider is not trying to drown you in vanilla.
A Few More Clouds (and Cloud Providers) to Ponder
What types of cloud computing would you trust with your ERP software deployment? If you are considering managed hosting, are you looking for other managed services as well, such as cloud security services? Are you looking for a flexible data center for a hybrid cloud deployment, perhaps with pricing on a pay-as-you-go basis. Do you know your hardware and software needs? When you open a web browser on a corporate computer, do you know if any of your business data is kept in a public cloud?