
P21 Public Web Client Access – Who’s Your Proxy?
ERP systems have traditionally had a functionality-accessibility problem: ERP systems were highly functional, but not especially accessible – they normally required desktop fat-client applications for access, and these were often hamstrung by local access requirements, making applications far from mobile.
As internet architectures became more and more robust, the possibility of web browser-based ERP became a reality, with new ERP vendors designing and building their software around the browser, and legacy vendors systems hastening to retrofit their existing ERP systems to accommodate the browser-based future.

But this introduced a new problem – one of accessibility vs security: the high levels of availability increased the possibility that threat actors could access a company’s ERP system remotely, and cause havoc to company data.
Most load balancers make it relatively easy to have an app safely deployed publicly. Normally, you run a reverse proxy server that passes traffic to your web app. This obfuscates the info for the destination of the web app and basically acts as a secure gateway to the internal resource. At EstesGroup, P21 Web UI is protected by MFA via a reverse proxy to the identity provider as well. However, administration of the Prophet 21 application introduces additional challenges. The P21 web login page contains a gear icon.

If a P21 user clicks the gear, they can access the Middleware server URL value, along with its port.
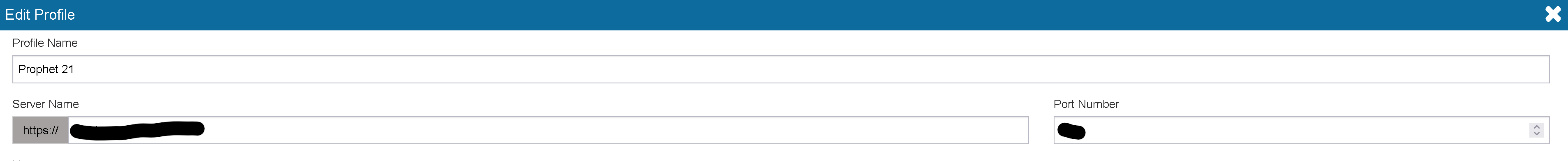
This introduces several complications:
- It basically shows users a free shortcut around MFA. A clever user can copy and paste the Middleware URL and port into their browser and access the P21 application directly, avoiding the MFA.
- The Middleware server URL and port are resolved on the P21 client side of the P21 application when logging in. This means, even though the Load Balancer can reverse proxy to the internal resource, it’s not going to be able to resolve the specific Middleware server URL on the P21 client side to complete the P21 login.
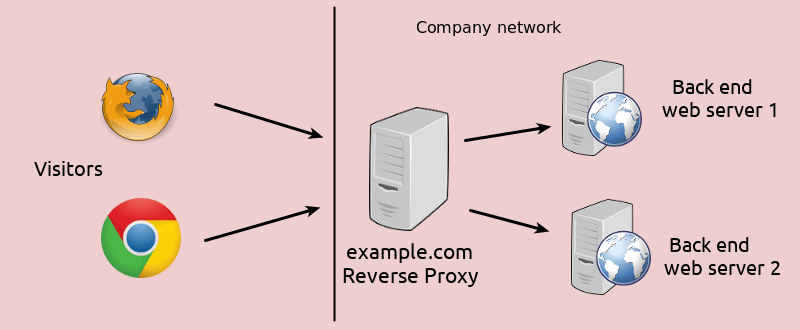
To get around these challenges, you might initially think to expose the Prophet 21 Middleware server to the internet and add a public DNS entry for it. But to directly expose P21 Middleware servers to the internet in that manner is a monumental risk. Another option is required.
To address the above issue, we do the following:
- We create a middleware reverse proxy to direct traffic to the middleware servers.
- We direct the P21 Web configurations to use the middleware proxy for its respective Middleware Server.
- We then expose the reverse proxies to the internet, creating DNS records for each of them.
By exposing the Middleware server proxies to the internet through a public DNS instead of the middleware servers themselves, you add a line of defense to the servers, only passing that needed traffic and keeping P21 Middleware Servers from being directly internet-exposed.
Another advantage of reverse proxying is the ability to intercept direct-access attempts. Theoretically, one might try to plug in the Middleware proxy URLs publicly and get access to the P21 API or the P21 Web UI. The reverse proxy allows for the functionality to block certain endpoints, such as the API or web client. When a user sees the Middleware URL in the P21 login settings, if they try to get around MFA and plug that URL in, they get a lovely 403 page, keeping them out of the Middleware. Alternatively, you can also redirect them back to the Web UI home page.
While there are other solutions for increasing accessibility, such as accessing through a VPN, these can at times be unreliable. If you are a decentralized company, with remote employees all over the country, speeds over VPN can be less than ideal on many occasions. Obviously, there are certain risks to opening any resource to the internet. It’s important to consider the attack surface, and the associated risks. At EstesGroup, we isolate any resources open to the internet, and implement Antivirus, Firewalls, and Threat Protection for all endpoints. Along with that, oftentimes, Geofencing helps cut out a lot of noise on any resource open to the internet, to prevent overseas attackers using botnets.

Marshall Douglas, EstesGroup Systems Engineer

