Epicor MRP Keeps You On-Time and Customers Happy
ERP! ERP! How do I love thee? Let me Count the Ways: A Robust Materials Resource Planning ( MRP ) Engine

One of my favorite movies growing up was The Wizard of Oz. One of my favorite scenes was when the “Wizard” was exposed as the “man behind the curtain,” pulling levers and revealing the secrets of the kingdom. In the business world, this phrase has morphed into meaning a person who elusively controls the intricacies of a large enterprise—and no one really knows the who, what, when, or how of the magic behind the success. MRP (Materials Resource Planning) is like this “man behind the curtain.” Incredibly powerful, MRP manages the forces of supply and demand, keeping everything under control.
There are basically three questions that a manufacturer has, and MRP answers:
- What does the customer want?
- How many do they want?
- When do they want it?
While those three questions seem relatively simple in nature, executing them in an efficient and profitable manner can become an extremely daunting, or even impossible task if you don’t have the correct tools. Fortunately, the Epicor MRP Engine is a highly sophisticated but user-friendly process that can help companies increase on-time performance, lower inventory and improve efficiency. MRP takes all three of these questions and looks at them holistically, to manage all variables that can occur on a shop floor.
What product does the customer want?
To answer this, MRP first looks to see if the part is purchased or manufactured. At the core of the system is the type-attribute of the part. Epicor defines a part in three ways: purchased, manufactured or sales kit. Purchased Parts can have a defined lead-time and are used in determining when product can be available if stock is not available. Manufactured Parts are built-up with routings and bills of materials. MRP will take into account the time it takes for each operation, dependent on the quantity and material availability, to determine when the product will be available to ship, based on capacity on the shop floor. Sales kits can be a combination of purchased and manufactured Parts and will use either or both types of logic to determine availability.
What quantity does the customer need?
Based on demand from forecasts or actual Sales Orders, the system looks at the current inventory level. If there is insufficient inventory, it will suggest to the Purchasing Department to buy some if it’s purchased or will suggest to the Planning Department to create a job to make some, if it’s manufactured.
What is the customer’s timeline?
This is where the Epicor MRP logic will take the first two questions and analyze two things: If we don’t have it in stock, can we buy it in time to deliver it, or do we have enough material and resources available to build how many they want? And it does this by taking into account not just one particular Sales Order, but all of the Sales Orders, and all of the inventory stocking levels and Job demands within a plant. Obviously, this is a very tall order, and in a dynamic manufacturing environment, things are often changing on a daily, if not hourly, basis. Because the MRP process can be such an intensive hardware resource demand, Epicor can be configured to run on a schedule (often times at night), either by looking at net change (to only work on those things that have changed since MRP was last run) or by being regenerative (to recalculate all demand).
Epicor also has the ability to run MRP for a specific part. Have a customer that needs a part ASAP? Now instead of having to wait for MRP to run, management has the ability to see the potential status of a job in a matter of minutes, and not hours, as MRP only has a single part to analyze. The MRP process can also be limited to a plant, product family, or commodity class—reducing the time and resources required to generate the needed supply records. Epicor MRP also supports multi-level pegging, which gives users the ability to trace the supply to each discrete source of demand. This process also drives the projected Sales Order shortages and is an incredibly powerful tool to manage customer satisfaction.
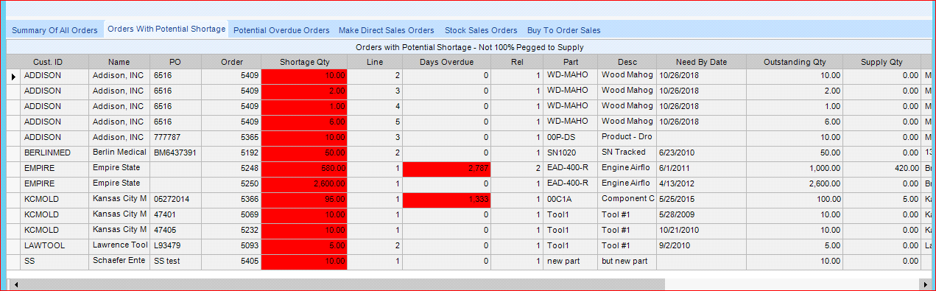
The Epicor ERP system, in conjunction with its versatile and powerful MRP process, allows your organization to “see behind the curtain” at an organizational level, revealing what the current demands for your products are and if you have the necessary supply to meet demand in a timely and profitable fashion.
There are lots of things to love about Epicor’s E10 ERP application.




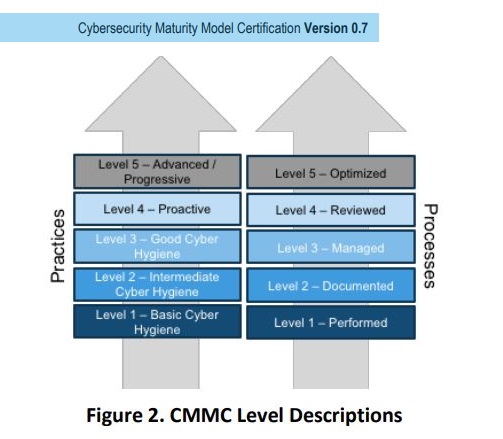
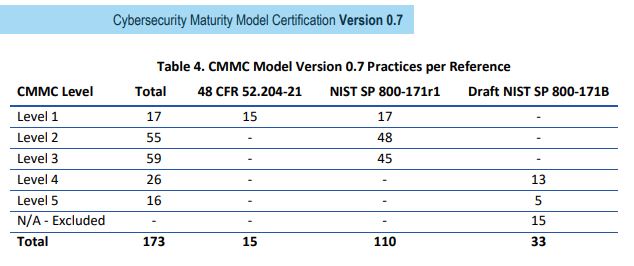
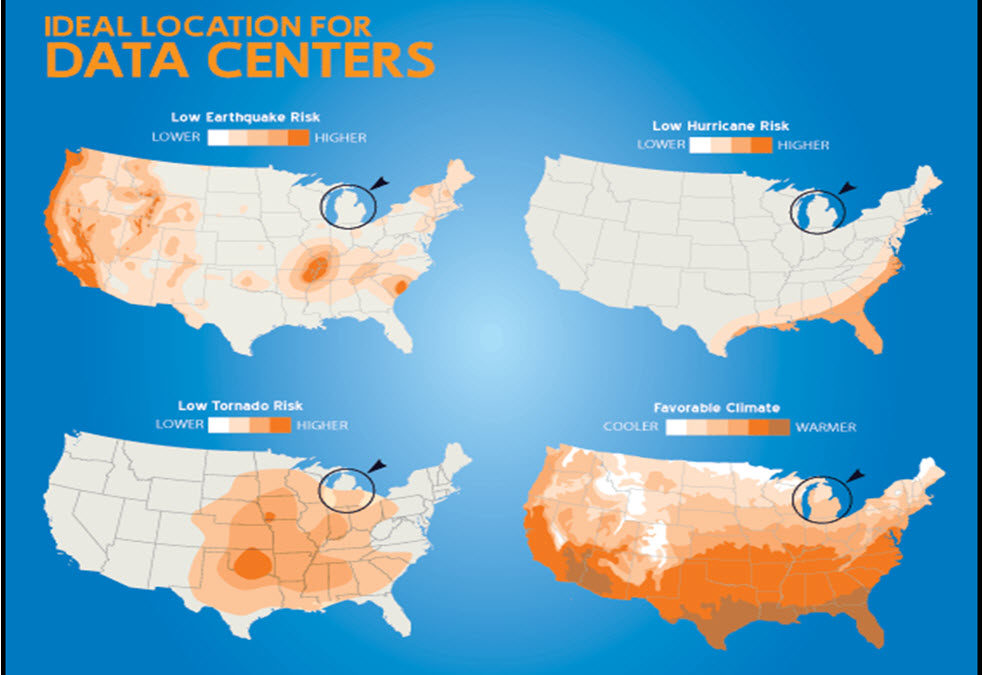
 For manufacturing companies, the advent of “cloud computing” has raised a lot of questions. Luckily, you don’t have to wander lonely as a cloud to find answers to your questions surrounding
For manufacturing companies, the advent of “cloud computing” has raised a lot of questions. Luckily, you don’t have to wander lonely as a cloud to find answers to your questions surrounding