Manufacturing Cybersecurity by the Numbers
Old Cyber Risks, New Cybersecurity Rules
Longtime NHL coach and living legend Scotty Bowman once famously claimed that “statistics are for losers.” For a game filled with numbers, that was a pretty bold statement. Around the same time, business author Peter Drucker, a legend in his own right, argued the opposite point, saying “if you can’t measure it, you can’t improve it.” There is certainly something to be said for “the bottom line” — the final score of a game is ultimately the most important number.
But a compelling case can be made that a winning game, a winning team, or a winning organization is comprised of many discrete elements, and that by seeking to measure and improve these key elements, the overall system will benefit accordingly. Our contemporary Moneyball sports world rendered Bowman’s statement a quant anachronism. Similarly, in the business world, managers and executives increasingly look for metrics that help them understand their areas of responsibility.

“Running the numbers” is not a substitute for successful management, but can be a valuable tool in its execution.
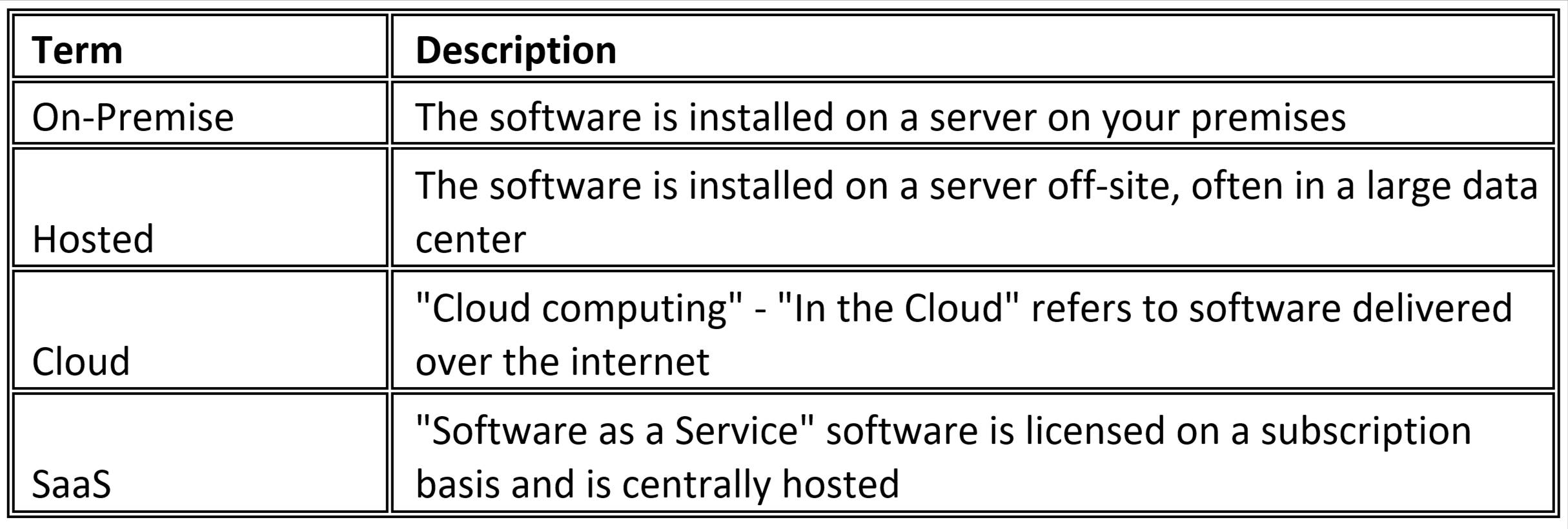
On that note, the National Institute of Standards and Technology (NIST) published a list of “20 Cybersecurity Statistics Manufacturers Can’t Ignore” which details some of the critical numbers that separate winning companies and organizations lost to the nefarious designs of malware, hackers, ransomware and the varying forms of cybercrime. From this list, a few highlights immediately come to the fore. By listening to the information embedded in the data, organizations can act quickly to mitigate the biggest threats that they didn’t know they had. A good manufacturing cybersecurity strategy can address old problems, predict new ones, and keep all operations cyber safe.
Ransomware Remains a Primary Threat to Manufacturers
The impact of ransomware on businesses has been monumental. According to NIST, 1 in 5 small or medium-sized businesses (SMBs) report that they have fallen victim to a ransomware attack. This makes ransomware the number one threat to organizations. Ransomware is unique among attacks in that it does not seek merely to damage the resources within a network. Rather, a ransomware attack encrypts company files, making them inaccessible to the organization and its users. Access to the decrypted files is only provided once payment to the assailant has been made.
The effects of ransomware are immediate. When a company gets ransomed, all operations affected by the encrypted files come to a grinding halt. This has a cascading effect across the organization as it struggles to stay open during the crisis. This often results in delayed production, late shipments, confused inventory levels, and frustrated customers. To cope with the outage, the company normally resorts to a handful of painful workarounds that are difficult to unravel and clean up once the ransom has been paid.
Ransomers Attack & Manufacturing Cybersecurity Teams Rally
In DoD environments where data cyber security is key, the impact to a company’s reputation can be detrimental. As such, it is no surprise that a ransom situation can cause an organization to go out of business entirely. Worse still, the costs are increasing. According to NIST, over the course of a single quarter in 2019, the average ransomware payment went up by 13% to $41,198. The impact on an SMB’s cash flow should be self-evident. Hackers know no limit when it comes to ransomware targets, attacking companies of all sizes. For that reason, there is no reason to believe that your organization can hide under the hacker’s radar. Therefore, manufacturers across the nation are increasing their investments in enterprise risk management and security solutions.
Microsoft Office is a Primary Vehicle for Malware
Microsoft Office has been a mainstay of organizations large and small. But the security risks of Microsoft files in an unmanaged environment are considerable. According to NIST, 38% of malicious file extensions come from Microsoft Office formats such as Word, PowerPoint and Excel, making this the most common set of file extensions. Microsoft’s Office suite has long been entrenched in the daily life of SMBs and manufacturers. Shop schedulers frequently define and redefine priorities using spreadsheets, SOPs utilize document formats for process control, and presentations to a company’s staff routinely take the form of a PowerPoint presentation.
While these file formats are common, they are far from invulnerable, and the robust capabilities that Microsoft created within each format provides opportunities to embed hostile code that can detonate once the files are saved within the network parameters of an organization. And file sharing across the manufacturing community is widespread. It is common, for instance, for vendors and presenters at manufacturing conferences and trade shows to hand out flash drives containing promotional materials. Manufacturing cybersecurity policies need to include these activities because should these files be infected, the consequences of introducing them to an unprotected company network could be catastrophic. As such, companies need to take care in managing the devices that connect to network, and the safety of the files they contain.
Social Media Accounts Become a New Target
Social media is widespread, and manufacturers are increasing playing along in order to get more visibility for their products and more interactions with their customer base. But with the proliferation of online social interactions comes increasing risk. In fact, 63% of MSPs anticipate that hackers will increasingly target social media accounts, according to NIST. Similar to Microsoft Office, social media toolsets have increasingly found their way into organizations. Initially thought of as a distraction, these toolsets have become embedded in many organizations, allowing for more collaborative communication between suppliers, customers, individuals, and groups.
Like the Microsoft Office suite, social media platforms have been enhanced and expanded, with new capabilities added on a routine basis. But a single compromised account can compromise an entire network when accessed from within the network’s parameters. Worse still, given the continually evolving nature of social media platforms, the threats are similarly evolving. Business owners need to understand what role social media will play in their organizations, and how these platforms can be leveraged without excessive risk. Manufacturing cybersecurity measures should take into account all accounts, including those on Twitter, Facebook, and similar online social meeting grounds.

When it comes to cybersecurity for manufacturers, the numbers don’t lie.
The correlation between successful IT threat mitigation and business success is well documented. Understand the numbers and take the necessary actions to put the odds in your favor. Manufacturers can avoid a cyber security breach by taking it one step further by partnering with industry experts: managed services firms with cyber specialists lead the way in cyberattack mitigation.