You already know you need protection from the cybersecurity threats circulating the market, but you might not have the time to know the specifics—like what endpoint security is or why you need it. If you have devices accessing a network, then you have an endpoint that needs protection. This elusive endpoint is simply any device that interacts with your network—the touchpoint between your network’s perimeter and the outside world. The bring-your-own-device (BYOD) movement that’s currently shaping the business world makes network security challenging because it creates a high demand for comprehensive endpoint security. You need to protect your customers and your business by protecting your team, and this begins with endpoint security.

Bring Your Own Disaster
The BYOD movement introduces a number of specific challenges in securing networks. The proliferation of devices interacting with a network, both in kind and in number, increases the number of endpoints and thus also increases the potential vulnerability of a network. Each new endpoint is a potentially exploitable gateway. The propagation of vulnerabilities demands a solution that can address this new circumstance. The solution that companies are increasingly utilizing to address their evolving needs has come to be known as endpoint security. Endpoint security helps ensure that all devices interacting with a network are compliant to the necessary security standards, protecting both the network and the devices themselves.
Endpoint security differs from traditional antivirus in the way that it detects and responds to threats. Traditional antivirus operates by comparing a program’s signature to a database of known malicious programs. Programs flagged as malicious would be stopped by the antivirus agent. This method of threat prevention is, by design, a step behind the attackers. Traditional antivirus can only detect malicious programs that have already been logged in the antivirus agent’s database. This creates problems in detecting new threats—what are sometimes called zero-day attacks. This also creates problems with newer “signatureless” attack methodologies that work to obscure their signatures, to work around the known signatures that antivirus looks for.
The question here is one of prevention vs. one of detection: antivirus focuses on preventing attacks. While this sounds logical, the tools available at its disposal, as we have seen, are limited. Should a malware attack slip through, antivirus is ill-equipped to deal with it once it’s inside the network. This brings in the need for more dynamic, behavioral-based detection methodologies that can leverage artificial intelligence and machine learning to detect suspicious application behaviors and react accordingly.
Leveling Up
Modern endpoint security platforms operate in a multi-level manner, protecting networks and network devices in multiple phases of vulnerability and response.
- The pre-execution phase: This level is for threats as they enter the network.
- The on-execution phase: This step is for threats that have entered the network and are in the process of acting out their program logic.
- The post-execution phase: This involves the steps to mollify threats that have executed.
Combining static prevention with dynamic detection, modern endpoint security platforms leverage machine learning to detect threats on execution. This becomes beneficial, not only for signatureless attacks, but also for “file-less” attacks that are operating exclusively in memory.
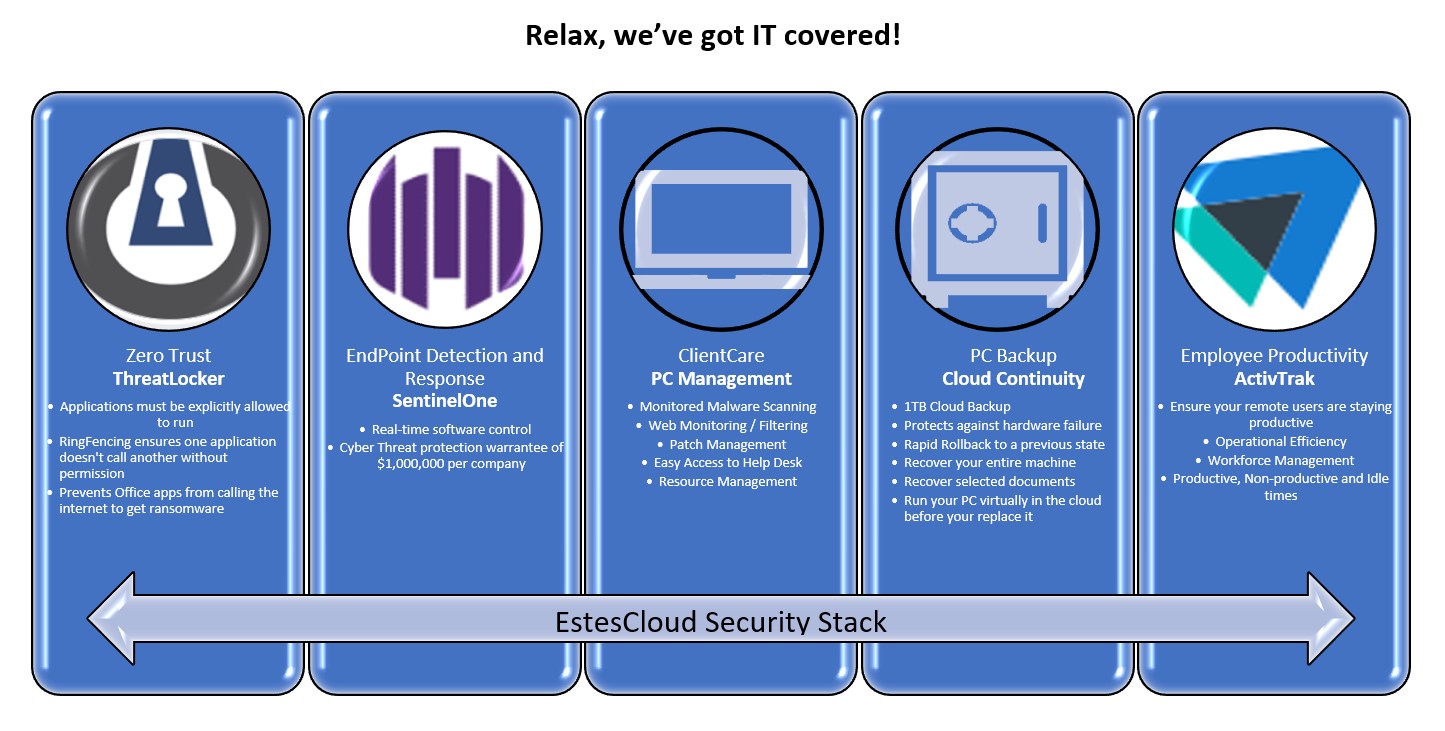
As part of our EstesCloud security stack, we work with several vendors to provide broad and comprehensive endpoint detection and response. AI, combined with our SOC (Security Operations Center), provides the level of endpoint security that cannot be addressed by traditional antivirus. Our cybersecurity solution comes with a strong warranty—cyber threat protection provides you with financial support of $1,000 per endpoint, or up to $1 million per company, securing you against the financial implications of a ransomware attack if your company indeed suffers an attack and our team is unable to block or remediate the effects.

