Remote Workforce Security
Securing Your Devices to Protect Your Data Get a FREE Remote Workforce Security Assessment NOWAre your remote workers secure?
Are you protected?
In this webinar, EstesGroup’s VP of Technology Services, Daryl Sirota, shares the critical steps business owners and employees must take to secure data using centralized cyber security solutions while working away from traditional company office culture. Find out how to abide by regulatory compliance when workers are displaced or disbanded (or when simply living the life of a digital nomad).

Watch the Presentation
“Remote Workforce Security”
Presented by EstesGroup with the Loveland Chamber of Commerce
Your data protection begins with you. A good cloud provider is your most critical resource for data backup and disaster recovery planning when your company is dependent on remote workers!
How to Work From Home
Home security systems protect you from physical intruders.
Data loss or identity theft?
You need more than a motion light and a sprinkler.
How to Stay Secure in Public Spaces
At an airport, a coffeeshop, a hotel, or a public park?
On the move or on the sofa?
Learn what you can do to secure your data anywhere.
Security Solutions are Adapting to Remote Work Culture
Remote worker security begins with awareness and training. Threat vectors happen, but cybersecurity victories do, too. If you know how criminals can access your information, you know where to build your fortresses.
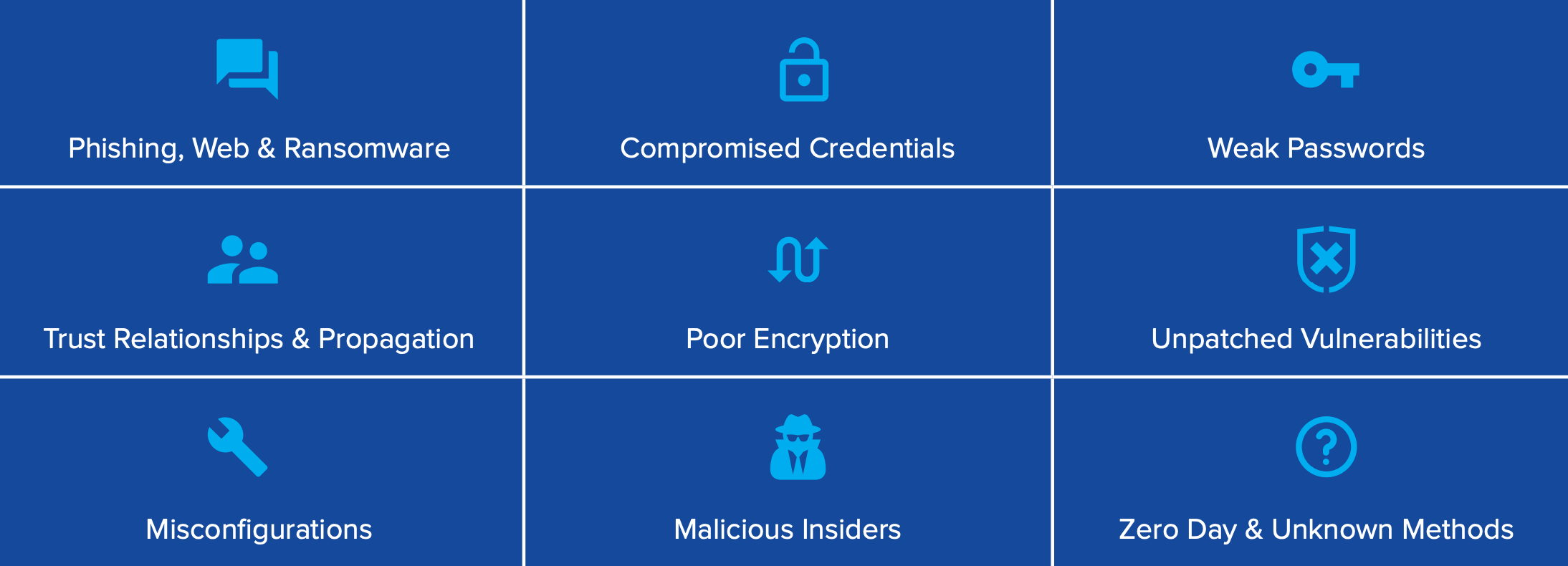
Cyberthreat Vectors
(how the hackers get in)
Phishing, Web & Ransomware Compromised Credentials Weak passwords Relationships & Propagation Poor Encryption Unpatched Vulnerabilities Misconfigurations Malicious Insiders Zero Day & Unknown Methods
Security and Data Protection Now Begins at Home
Even if you go to the office every day, you might have work email, or a similar app, installed on a mobile device. Securing traveling devices becomes a dance around Wi-Fi stranger danger and friendly shoulder surfing.
Cyber Dance Victors
(how to jitterbug around trap doors)
Install updates as they happen, including antivirus and anti-malware tools.
Clear your devices of programs that aren’t necessary.
Keep your connections secure, and keep your devices locked.
Use password managers, secure browsers, and stay alert to potential threats.
$36,000
Average cost
of a ransomware attack
197 Days
Average time
it takes to surface a data breach
19 minutes
Average time
it takes a skilled hacker to attack
Your Business is the Security Bridge
Small businesses, big businesses, just-right businesses… No matter the size of your company, you provide the shelter for your data. You also provide bridges of stability for corporate communication. Cybersecurity serves as the foundation for these safe pathways that support and build the community of teamwork and partnership that your growth and success depend on.
Do you struggle with any of these common security shortfalls?
- Security and IT infrastructure funding
- Low IT skill or inadequate support for key talent
- Aging equipment or unpatched devices
- Overworked employees
- Untrained staff
58% of cybercrime victims are small businesses. New threats target 100% of us. EstesGroup wants you to protect your family, your friends, your data, and your livelihood by adapting to the pervasive culture of the dark web.
Would you like to learn more about cybersecurity trends and solutions?
Please sign up for our IT newsletter to get technology advice delivered monthly to your inbox.
[pardot-form id=”2665″ title=”Newsletter”]

