Security Audit & Network Assessment
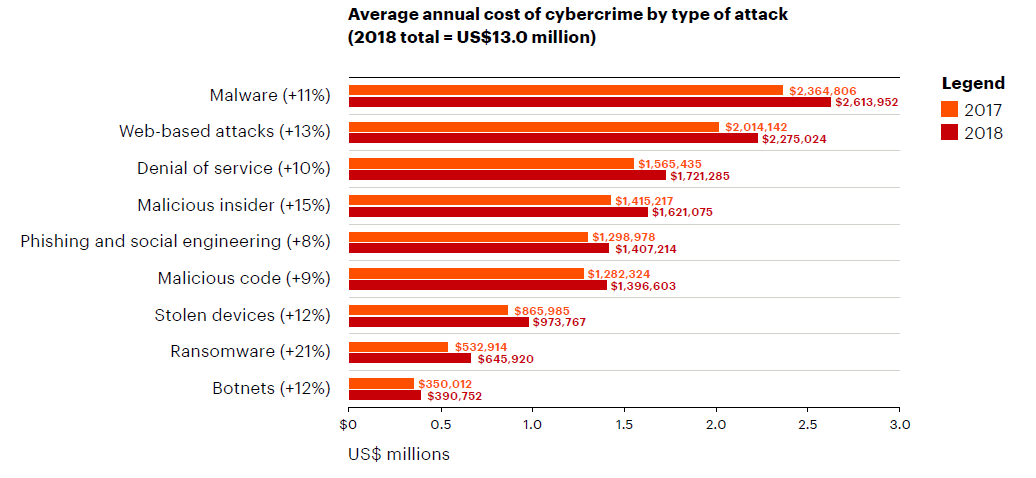
CLOUD-BASED SECURITY SOLUTIONS FOR YOUR BUSINESS9 out of 10 computer networks have potentially serious IT problems sitting undetected.
Are you wondering if your IT systems are safe from cybercrime?
As a leading provider of IT services, we perform in-depth health assessments of computer networks and business technology. In a Security Audit and Network Assessment, we will analyze your network to identify vulnerabilities that could leave your organization at risk of a business interruption. Depending on what we uncover, we will make suggestions on ways to prevent unauthorized access, augment security systems, better lock down sensitive data, become more mobile, and get more out of your existing technology infrastructure.
Our Unique Process Has Many Benefits Over Other Security Assessments
- No software installed, so no one needs to know, including your current IT provider.
- No agents or probes living on your network for days, weeks, or longer.
- An average, mid-sized network is scanned quickly, taking around 30 minutes to get the job done.
We Check What You Want Us to Check
- Servers
- Workstations
- Printers
- Non-Active Directory (AD) Devices (like Switches, Routers, Printers)
- All Software Applications
We Uncover What You Need To Uncover To Stay Safe Online
- External issues which put your network at risk of business disruption or data loss
- Detailed breakdown of Active Directory Security Group Membership
- Systems missing anti-virus, anti-spyware, or unsafe firewall configuration
- Old computers which are still joined to your domain or have not been removed
- Systems missing patches, service packs, or requires security updates
- Local accounts with weak or insecure passwords
- Security Policy inconsistencies across the network servers and computers
- Outbound system accesses that should be blocked
- Lack of content filtering (social media, entertainment, explicit content, illegal download accesses)
- Unsafe or poorly configured user access to network shares
- Old user accounts which still have access or have not been properly disabled
- Internal systems with open ports that pose a potential security risk
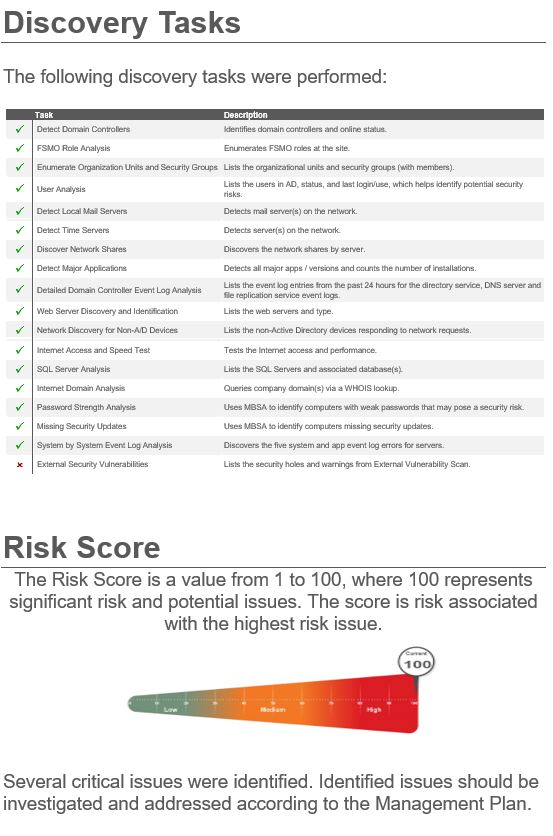
Executive Report Findings
Once the assessment is completed, you will receive a 6-8 page Executive Report with an overview of the devices on the network along with a network Risk Score and analysis of each potential issue we uncover. The report includes a full detailed network inventory, user documentation, and all vulnerabilities identified. We will review this document with you to discuss the findings in detail, and answer any questions you may have, as well as discuss the next steps for your company’s continued cyber security.
Are you interested in a Security Audit & Network Assessment for your company? To start your company’s vulnerability assessment, please fill out our form below or chat with us now.
58% of Cyber Attack Victims are Small Businesses, with less than 250 employees.