The Ancient Art of Specifying Report Requirements in Epicor
Designing Custom Reports in Epicor ERP
Creating custom reports in any Enterprise Resource Planning (ERP) system, including Epicor Kinetic, can be a surprisingly difficult endeavor. I’ve seen numerous cases in custom report development where the final deliverables did not match the expectations. Why does this happen? Most often, it’s not due to technical challenges but rather the difficulty in defining what you actually need.

If you are considering creating a custom report and are in the process of specifying report requirements in Epicor, there are a few things to keep in mind.
When requesting a custom report in Epicor ERP, simply providing a paper copy of a report from your legacy system and asking the developer to recreate it in Epicor is not enough to ensure a successful outcome. While the legacy report may serve as a starting point, it’s essential to recognize that the data structure and available fields in Epicor may differ from your previous system. To create an effective custom report, you need to provide more specific details about your requirements, taking into account the unique features and capabilities of Epicor ERP. Similarly, offering a one-line description of your desired report and expecting the developer to “get it done” is insufficient for achieving the desired results. A brief, vague description leaves too much room for interpretation and can lead to misunderstandings. So, make note of these two things not to do when planning your approach:
- Simply pulling out a paper copy of a report from the legacy system and saying, “Do it in Epicor,” is not sufficient.
- Providing a one-line description and saying, “Get it done,” is also inadequate.
Key Elements for Specifying an Epicor Report
To ensure your custom report meets your expectations, consider the following key elements:
Query Logic
What should the underlying query return? For example, specifying the report logic might involve “all active parts of Part Class X” or “all sales order miscellaneous charges that have not yet been invoiced.” Providing this basic logic helps the developer structure the underlying query.
Filters
Do you need to run the report filtered by something, such as the part, supplier, or site? If so, note it, as this will affect how the report is created.
Groupings
How do you want the data in the report grouped? For instance, you may want the data grouped “by site and customer.”
Sorts
Within the groupings, how should the data be sorted? This will impact how the underlying query is structured before the data is passed to the report designer. For example, you might want to “group by site and customer, and sort by invoice number” or “sort alphabetically by part number.”
Fields and Field Order
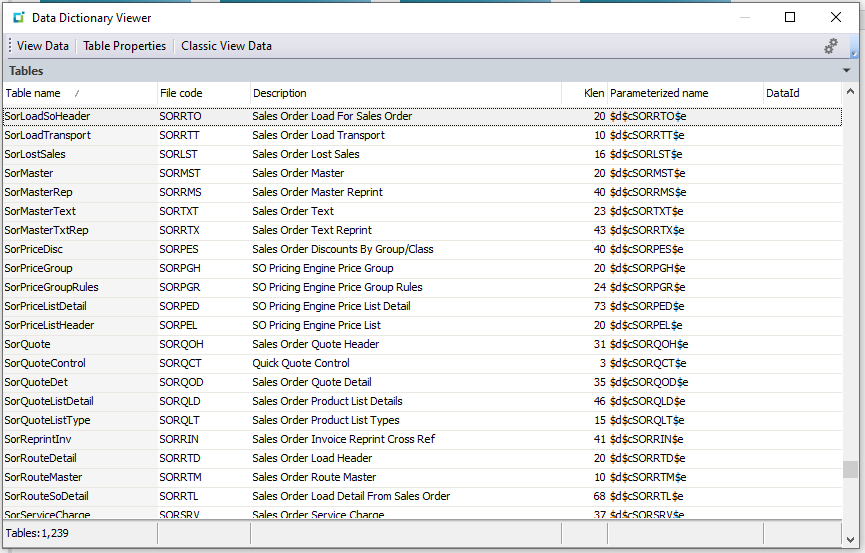
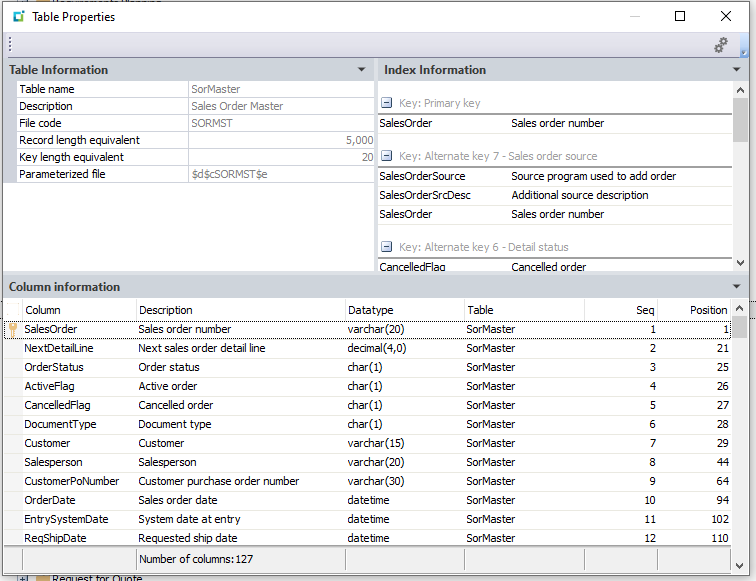
It’s important to know the specific ERP fields where the data lies, and the order they should appear in the report. If it’s a calculated field, you need to provide the calculation (e.g., past due = due date – current date).
Sample Data
Often, to build a report, you will need the underlying data in the development environment. For example, if you are specifying a report that collects all miscellaneous charges, you may need to create some sales orders and sales order lines with miscellaneous charges.
Mockup
Providing a visual mockup of what you are looking for helps the developer organize the output. If you are replacing an existing report from a legacy system, this may be a good time to use the legacy report copy, albeit with the necessary edits to make it specific to the new ERP system.
When defining report requirements in Epicor ERP, it’s crucial to provide clear and detailed specifications to ensure the final output meets your expectations.
Epicor report requirements should include query logic, filters, groupings, sorts, fields, sample data, and a visual mockup to guide the developer in creating a custom report that aligns with your business needs. By effectively communicating your Epicor report requirements, you can streamline the development process and obtain the insights you need to make informed decisions and drive your business forward. Creating custom reports in Epicor ERP can be a complex process, but by understanding and addressing the key challenges, you can ensure your reports meet your specific needs. The most significant hurdle is often not the technical aspects but rather the difficulty in clearly defining your requirements. By providing detailed specifications, you can help bridge the gap between your expectations and the final deliverable. Remember, effective communication and collaboration are essential to overcoming challenges.