
Electronic Signatures (eSignatures) in SYSPRO
A “Signature” SYSPRO Admin Tool
Electronic Signatures (also referred to as eSignatures) is one of SYSPRO’s most powerful administrative tools. It allows you to audit and monitor transactional data against any type of event you can imagine throughout SYSPRO. In addition, it also includes “trigger” features where you can have certain events execute custom scripts, send email messages, or invoke custom reports. This section of SYSPRO has several layers of functionality. Explaining it all is difficult, so we have highlighted below some of the key features that eSignatures have and how you can use them to improve your SYSPRO experience.

Auditing Capabilities
The most used feature of eSignatures would be the auditing capabilities that they possess. If you have used SYSPRO for a good amount of time, you may have come to find that it is hard to track down “who did what” and “when did it happen”. SYSPRO does not natively keep much information on file about who is committing changes to the system.
For instance, by default in SYSPRO, you will have a hard time figuring out who created that one purchase order, who completed that job prematurely, or who modified the price of that sales order line. eSignatures exist to solve exactly that!
In the Electronic Signatures Setup program, you can browse on any type of event across all SYSPRO modules. Against each of these specific events, you can set up access levels, custom triggers, and detail logging of key data points relating to these events when they take place throughout SYSPRO. As an example, under the “Sales Orders” module, you can add a logging condition against the “SO add sales order” transaction to keep a log of any operator who creates a sales order in SYSPRO.
Each time a sales order is created, a log entry is then stored in the database with details about who created the sales order, when they created it, and which details the sales order was created with. You can query eSignature event logs by using the eSignature Query program later for auditing purposes.
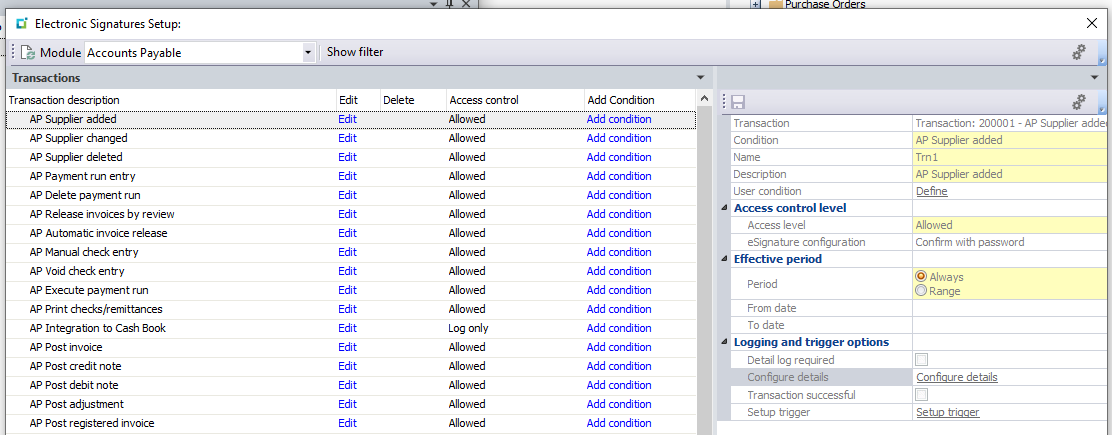
Additionally, there are also “e.net” type transactions for the same events that track when business objects perform these events. These can be extremely helpful if your environment uses any third-party products or custom business object implementations. There are otherwise no other efficient ways in SYSPRO to monitor or track changes that are committed by business objects unless your custom integrations have been programmed to track it themselves.
SYSPRO eSignature Triggers
Triggers can be configured against an event to perform a certain action. Contrary to the logging, these are helpful if you are looking to perform an additional action when an event takes places. When setting up an eSignature Trigger, you can choose between the following trigger action types:
- Run a VBScript
- Run any program
- Run any application
- Write to message inbox
- Run an SRS report
You can probably already start to imagine the countless things these could be useful for. For instance, perhaps you want to receive an email whenever a new customer is created in SYSPRO. Maybe your programmer wants to run a script and perform a given activity if the event was triggered by a specific operator, roles, or group. Or maybe, you want to run an entirely custom-built program and pass it the sales order number that was just created and captured by the eSignature.
These details only scratch the surface of what is possible with eSignatures in SYSPRO. There are several additional features within this section of SYSPRO that may be worth your time to investigate and get familiar with as they can take your company’s SYSPRO experience to the next level.
Your SYSPRO Autograph
Electronic Signatures (eSignatures) emerge as a cornerstone of SYSPRO’s administrative arsenal, delivering robust functionalities to enhance the overall user experience. The auditing capabilities stand out as a pivotal feature, addressing the longstanding challenge of tracking changes within SYSPRO. By meticulously logging key data points related to various events across modules, eSignatures enable users to easily trace actions, such as the creation of purchase orders or modifications to sales order prices. The Electronic Signatures Setup program empowers users to establish access levels, custom triggers, and detailed logging, offering a comprehensive solution for auditing purposes.
Furthermore, the versatility of eSignature triggers adds another layer of efficiency, allowing users to configure actions such as sending emails, running scripts, or generating custom reports in response to specific events. As we delve into the intricacies of eSignatures, it becomes evident that the possibilities extend beyond the surface, with additional features waiting to be explored. By investing time in understanding and leveraging the full potential of eSignatures, businesses can elevate their SYSPRO experience, ushering in a new era of efficiency and control.













