12 Days of ECHO, Tenth Day: My Admin Gave to Me, Epicor Performance and Diagnostic Tool Checks!

SQL and the Reporting Engine
Epicor ERP 10 provides the Performance and Diagnostics Tool as part of your Epicor Administration Console. While the tool is often installed when setting up an E10 solution, it’s often forgotten about afterwards. The full tool has lots of capabilities, but I’d like to highlight the “Config Check”.
When first run, you have to go to Options-Settings and define which E10 application you are going to check, along with the Epicor username/password to access the data.
Then, click the “Check Configuration” button and wait a few moments. The tool will go look at several parameters and find out which settings are Pass, Warning or Fail. Depending on your environment, you’ll want to qualify those warnings or failures, as they might not be as disastrous as it seems.
Here’s the output of one of our hosted Epicor servers running 10.2.500. Looks like there might be something wrong with the SQL Setup.
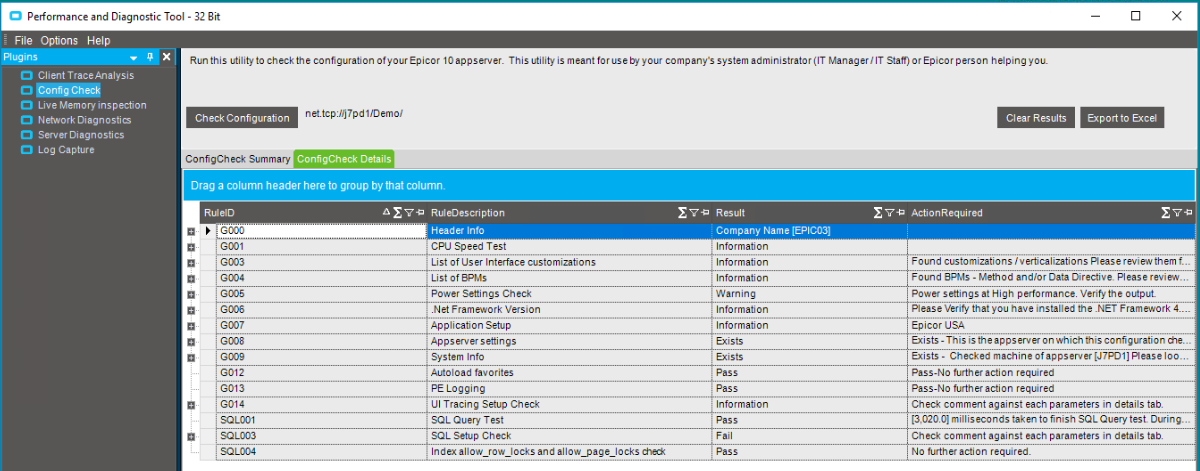
Using the ConfigCheck Details shows the underlying issues, in this case, there are several issues! Some of the red lines are problems (like I might not have enough space in the SQL MDF file), while others are not (SIMPLE recovery mode is not a problem for this application)
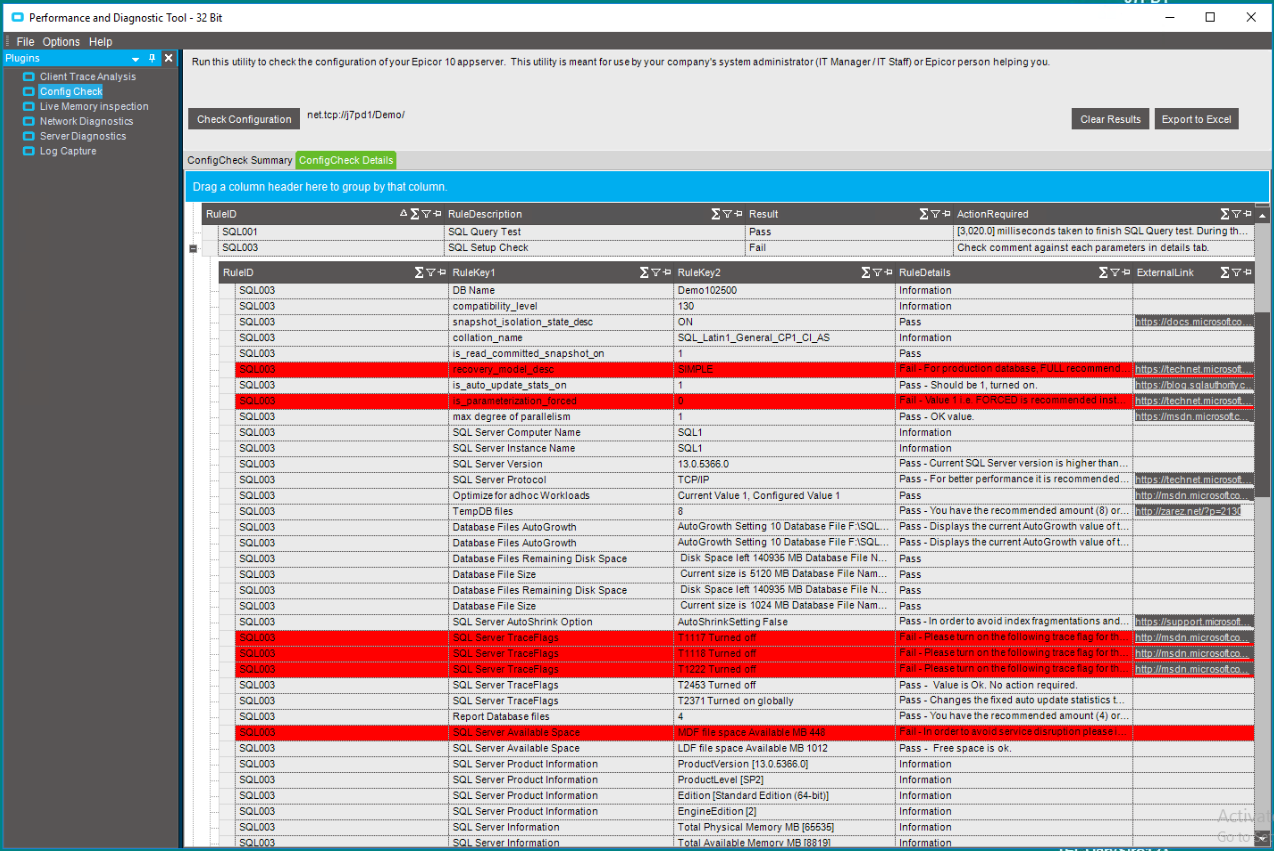
In any case, before I start tuning, tweaking and fixing, I always export the result to Excel so I have a record of what it looked like today. After I fix these items, I’ll re-run and re-export the check to show my client that the appropriate items were fixed. Of course, if items are flagged but not fixed, I’ll include an explanation of why. For example, Simple recovery mode on a SQL databases means I don’t have to worry about transaction log growth. (See our prior post “SQL Transaction Log Maintenance”)
If you need details on how to correct each issue, you can drill into the ExternalLink provided. Warning – many corrections will require downtime, so while you can run the tool anytime, correcting things will likely be during a maintenance window.
I recommend running this tool as part of a quarterly or annual basis just to help keep your Epicor E10 system running smoothly.
If you liked reading the “Tenth Day of ECHO” return to our main list to read all of the other “12 Days of ECHO” posts.